Overview
The Control Panel is a web-based interface that administrators use to configure and manage the RadiantOne Identity Data Management product. RadiantOne also offers a configuration API that can be called programmatically with an Access Token.
Accessing the Control Panels
The Control Panels utilize a web server that is installed with RadiantOne. The endpoint to access the Control Panel is defined when you create an environment in the Environment Operations Center. For details on creating environments and locating the Control Panel endpoint, see Create Environments.
The web browsers supported for using Control Panel are: Microsoft Edge Version 127.0.2651.98 (+), Google Chrome Version 128.0.6613.120 (+).

Classic Control Panel
To switch to Classic Control Panel, use the menu options for the logged in user in the upper right.
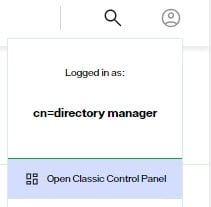
The currently logged in user must have permissions to access the Classic Control Panel.
For more details, see Configuration Changes that Require Classic Control Panel
Authentication
Username and Password
Log in using the directory administrator (cn=directory manager) as the user with the password you set during the install of RadiantOne. Once logged in, the Directory Administrator should navigate in the Control Panel to the ADMIN section and define other users needed to administer RadiantOne. A user can either use their full DN (if known), or their user ID. However, to login with just a user ID, you must configure a user ID to DN Mapping.
The Control Panel displays a message when authentication fails. The table below lists the possible error messages.
Message | Cause | Solution |
|---|---|---|
“Authentication failed. Reason: Access is denied.” | Incorrect login ID or incorrect password. | Verify the login ID and password and try again. |
"Authentication failed. Reason [LDAP: error code 49 - Password has expired.]" | The user's password has expired. | If the client application supports password reset capabilities, the user can reset their password. |
“Authentication failed. Reason: [LDAP: error code 19 - The password failure limit has been reached and the account is locked. Please retry later or contact the system administrator to reset the password.]” | The account is locked. | Retry later or contact the system administrator to reset the password. |
Last Login Time
The time the user last logged into the Classic Control Panel is displayed above the "Logged in as..." information shown in the top right.

MFA
Support for MFA logins, you must integrate with an OIDC provider that offers MFA. The MFA checking is handled by the OIDC provider. See the OIDC token configuraton below.
OIDC Token
The RadiantOne Control Panel supports SSO with your corporate Identity Provider using OpenID Connect (OIDC) token-based authentication. This option provides the security of sending user login credentials to the authentication server (the Identity Provider), not the application (Control Panel, the Relying Party). OpenID Connect token authentication allows you to send your username and password just once, to the Identity Provider (IDP), have MFA validated (if enabled and supported by the Identity Provider), and then pass the token in the request to the Control Panel. When OIDC is configured in RadiantOne, the Control Panel login screen displays:

The administrator must click the "Log in with Corporate SSO" option to login with an OpenID Connect token.
The high-level flow is shown below.

Detailed steps:
-
The RadiantOne Admin navigates his browser to the RadiantOne Control Panel and clicks “Login with Corporate SSO”.
-
The browser redirects the user to the OIDC Provider’s authorization endpoint with the necessary parameters (ClientID, redirect URI, scope).
-
The RadiantOne Admin authenticates to the OIDC server (if not already authenticated) and the OIDC server prompts the user for authorization: Control Panel wants to access info (scopes) about you. Do you Authorize this?
-
Admin user gives consent.
-
OIDC server gives Control Panel an Authorization code.
-
The Control Panel sends the OIDC server the authorization code and requests an ID token.
-
OIDC Server sends the ID token to Control Panel.
-
Control Panel uses the information in the token along with the Claims to User DN Mapping rules to locate the user in the RadiantOne namespace to enforce permissions based on what delegated admin role the user is a member of – which dictates what the admin is allowed to do within the Control Panel.
To enable support for OIDC authentication:
-
Have your client ID and secret (optional unless you are using Authorization Code Flow) associated with the Control Panel application configured in your OIDC server ready. The Redirect URL configured for the web application should point to the URL associated with the Control Panel. Example: https://rlqa-svc.dev01.radiantlogic.io/callback
-
Log into the Control Panel.
-
Navigate to Admin > Control Panel Configuration tab.
-
Select an OIDC Provider from the drop-down list. If you are using your own provider, select the Custom option.
-
Click "Discover Endpoint URLs". The Authorization Endpoint URL and Token Endpoint URL should auto-populate. If you configure a custom provider, you can enter the needed Authorization Endpoint URL and Token Endpoint URL. In OpenID Connect the authorization endpoint handles authentication and authorization of a user. In the OpenID Connect Authorization Code Flow, the token endpoint is used by a client to obtain an ID token, access token, and refresh token.
-
Enter the Client ID associated with the Control Panel application configured in the OIDC provider.
-
(Optional unless using Authorization Code Flow) enter the Client Secret associated with the Control Panel configured in the OIDC provider.
-
Select the Client Authentication Method corresponding to how the Control Panel client has been configured in the OIDC Server. There are two options available: CLIENT_SECRET_POST and CLIENT_SECRET_BASIC.
-
Select a value for Requested Scopes to display a list of possible choices: openid, email, profile..etc. Openid is required. You can add more if needed as long as they match the configuration of the client in the OIDC server. Click ADD SCOPE to add the selected scope to the configuration.
-
Click ADD MAPPING next to DN Mapping Expression. This configuration determines the logic to link the user that logs into the Control Panel with an Open ID Connect token with an identity in the RadiantOne namespace. This process determines which identity is used to enforce authorization within the Control Panel. The user mappings must result in a single user. If no user is found or if more than one user is found, the login fails. The RadiantOne user that is linked to the authentication token must be a member of a RadiantOne default or custom Delegated Administrative group.
-
In the OIDC to FID User Mappings window, click
Add. -
There are two options for identifying the RadiantOne admin user. If the RadiantOne user can be identified by using values/claims from the token to comprise the DN, use the Simple DN Mapping. If the RadiantOne user can be identified by performing a lookup in RadiantOne based on values from the token, use the Advanced DN Mapping.
-
Click SAVE.
Examples of configuring the Simple DN Mapping and an Advanced DN Mapping are shown below.
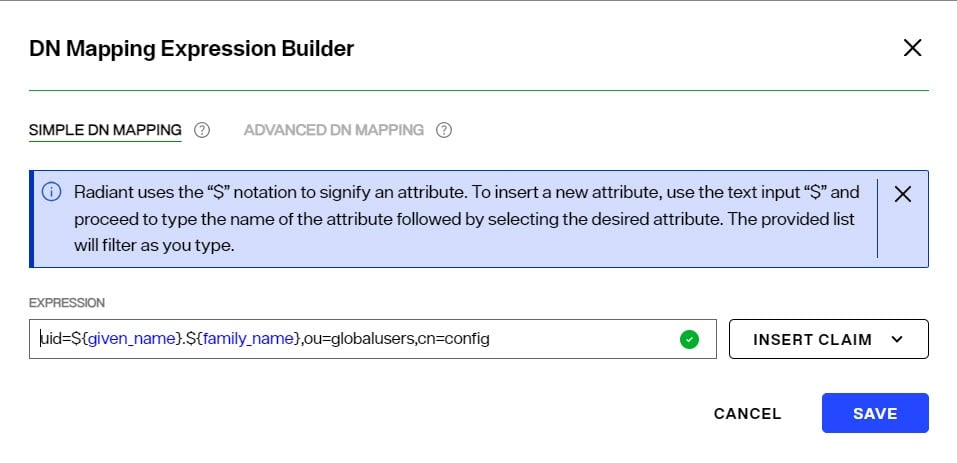
In the Simple DN Mapping example shown below, the RadiantOne user is identified by using the given_name and family_name claims from the token to compute the DN.
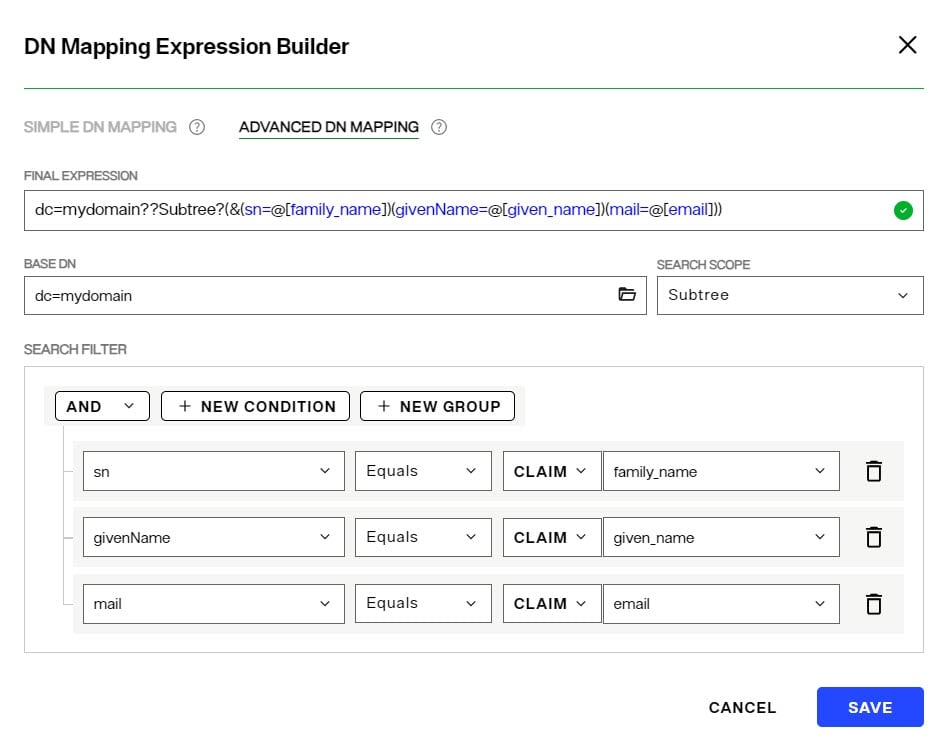
In the Advanced DN Mapping example shown below, the values of the family_name, given_name, and email claims from the token are used to condition a sub-tree search in RadiantOne, starting at the dc=mydomain naming context to locate the identity.
To disable support for OIDC authentication:
-
Log into the Control Panel.
-
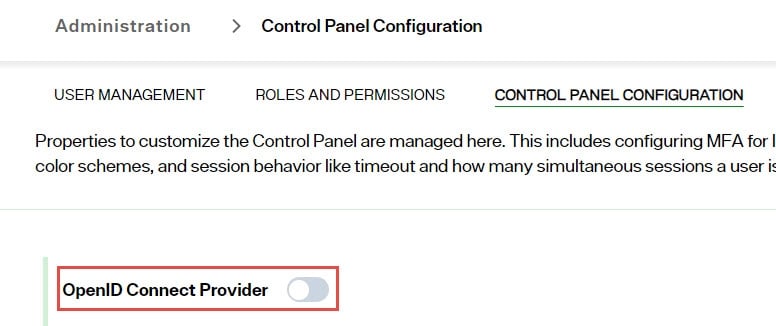
Navigate to Admin > Control Panel Configuration tab.
-
Click the Enabled toggle from on to off for the OpenID Connect Provider.
-
Click SAVE.
Authorization
Roles-based access controls are used to enforce privileges for Control Panel. Any user that can authenticate to RadiantOne can administrator the service if they belong to the proper group that is associated with one of the delegated administrator roles. RadiantOne includes default delegated admin roles that users can be assigned to. Custom delegated admin roles can also be defined. Roles & permissions are managed from Control Panel > Admin > Roles & Permissions.
Assigning roles to users is done from Control Panel > Admin > User Management tab.
Default Delegated Admin Roles
The default delegated admin roles can be viewed from Control Panel > Admin > Roles & Permissions. The default roles cannot be edited. However, you can use the default role definition as a basis for defining a new custom role by choosing the default role from the list when prompted to Clone Permissions during new role creation.
Directory Administrator: Members assigned this role can perform all operations (all operations that the other default roles can perform) in addition to being able to update username and password properties for data sources via an LDAP modify command.
Control Panel Config | Permissions |
|---|---|
SETUP > Data Catalog > Data Sources | View & Edit |
SETUP > Data Catalog > Template Management | View & Edit |
SETUP > Directory Namespace > Namespace Design | View & Edit |
SETUP > Directory Namespace > Directory Schema | View & Edit |
MANAGE > Directory Browser | View & Edit |
MANAGE > Tasks | View & Edit |
MANAGE > Security > Attribute Encryption | View & Edit |
MANAGE > Security > Access Control | View & Edit |
GLOBAL SETTINGS | View & Edit |
ADMIN > User Management | View & Edit |
ADMIN > Roles & Permissions | View & Edit |
ADMIN > Directory Manager Settings | View & Edit |
ADMIN > Control Panel Config | View & Edit |
ADMIN > Access Tokens | View & Edit |
ADMIN > Entry Statistics | View & Edit |
ACCESS CLASSIC CONTROL PANEL | Impersonate Role defined for cn=directory administrators,ou=globalgroups,cn=config |
Namespace Administrator: Members assigned this role are responsible for managing the RadiantOne namespace. The namespace is managed from Control Panel > Setup > Directory Namespace > Namespace Design. The responsibilities include:
- Creating new naming contexts and mounting backends
- Configuring and managing identity views
- Configuring and managing persistent cache
- Creating and managing RadiantOne directory stores
- Creating and managing synchronization pipelines
Control Panel Config | Permissions |
|---|---|
SETUP > Data Catalog > Data Sources | View & Edit |
SETUP > Data Catalog > Template Management | View & Edit |
SETUP > Directory Namespace > Namespace Design | View & Edit |
SETUP > Directory Namespace > Directory Schema | View & Edit |
MANAGE > Directory Browser | View & Edit |
MANAGE > Tasks | View & Edit |
MANAGE > Security > Attribute Encryption | View Only |
MANAGE > Security > Access Control | View Only |
GLOBAL SETTINGS | View Only |
ADMIN > User Management | View Only |
ADMIN > Roles & Permissions | View Only |
ADMIN > Directory Manager Settings | View Only |
ADMIN > Control Panel Config | View Only |
ADMIN > Access Tokens | View Only |
ADMIN > Entry Statistics | View Only |
ACCESS CLASSIC CONTROL PANEL | Impersonate Role defined for cn=namespaceadmin,ou=globalgroups,cn=config |
Schema Administrator: Members assigned this role are responsible for managing the RadiantOne LDAP schema. The schema is managed from Control Panel > Setup > Directory Namespace > Directory Schema. The responsibilities include:
- Creating new LDAP object classes and attributes
- Extending the RadiantOne LDAP schema with objects and attributes from data source (backend) schemas.
- Importing new LDIF formatted files to extend the RadiantOne LDAP schema.
Control Panel Config | Permissions |
|---|---|
SETUP > Data Catalog > Data Sources | View & Edit |
SETUP > Data Catalog > Template Management | View & Edit |
SETUP > Directory Namespace > Namespace Design | View & Edit |
SETUP > Directory Namespace > Directory Schema | View & Edit |
MANAGE > Directory Browser | View Only |
MANAGE > Tasks | View Only |
MANAGE > Security > Attribute Encryption | View Only |
MANAGE > Security > Access Control | View Only |
GLOBAL SETTINGS | View Only |
ADMIN > User Management | View Only |
ADMIN > Roles & Permissions | View Only |
ADMIN > Directory Manager Settings | View Only |
ADMIN > Control Panel Config | View Only |
ADMIN > Access Tokens | View Only |
ADMIN > Entry Statistics | View Only |
ACCESS CLASSIC CONTROL PANEL | Impersonate Role defined for cn=schemaadmin,ou=globalgroups,cn=config |
Security Administrator: Members assigned this role are responsible for managing access controls, password policies, and attribute encryption. Access controls are managed from Control Panel > Manage > Security > Access Controls. The responsibilities include:
- Creating and managing access controls
- Creating and managing password policies
- Managing attribute and LDIF file encryption
- Manage access tokens
Control Panel Config | Permissions |
|---|---|
SETUP > Data Catalog > Data Sources | View Only |
SETUP > Data Catalog > Template Management | View Only |
SETUP > Directory Namespace > Namespace Design | View Only |
SETUP > Directory Namespace > Directory Schema | View Only |
MANAGE > Directory Browser | View Only |
MANAGE > Tasks | View Only |
MANAGE > Security > Attribute Encryption | View & Edit |
MANAGE > Security > Access Control | View & Edit |
GLOBAL SETTINGS | View Only |
ADMIN > User Management | View Only |
ADMIN > Roles & Permissions | View Only |
ADMIN > Directory Manager Settings | View Only |
ADMIN > Control Panel Config | View Only |
ADMIN > Access Tokens | View & Edit |
ADMIN > Entry Statistics | View Only |
ACCESS CLASSIC CONTROL PANEL | Impersonate Role defined for cn=aciadmin,ou=globalgroups,cn=config |
Read Only: Members assigned this role can only view configurations. They are not allowed to edit anything.
Control Panel Config | Permissions |
|---|---|
SETUP > Data Catalog > Data Sources | View Only |
SETUP > Data Catalog > Template Management | View Only |
SETUP > Directory Namespace > Namespace Design | View Only |
SETUP > Directory Namespace > Directory Schema | View Only |
MANAGE > Directory Browser | View Only |
MANAGE > Tasks | View Only |
MANAGE > Security > Attribute Encryption | View Only |
MANAGE > Security > Access Control | View Only |
GLOBAL SETTINGS | View Only |
ADMIN > User Management | View Only |
ADMIN > Roles & Permissions | View Only |
ADMIN > Directory Manager Settings | View Only |
ADMIN > Control Panel Config | View Only |
ADMIN > Access Tokens | View Only |
ADMIN > Entry Statistics | View Only |
ACCESS CLASSIC CONTROL PANEL | Impersonate Role defined for cn=readonly,ou=globalgroups,cn=config |
Creating Roles
Custom roles can be created from Control Panel > Admin > Roles & Permissions tab.
- Click ADD ROLE.
- Enter the role name.
- (Optional) select an existing role to quickly clone/assign similar permissions to the new role.
- Click OK.
- Go through each set of permissions and assign the proper privilege: None, View Only, or View & Edit.
- Click SAVE.
Permissions
The permissions available for creating custom roles in the new Control Panel are not applicable to the Classic Control Panel. However, custom roles can be associated with a Classic Control Panel role to allow administrators the needed access to both the new and Classic Control Panels.
Classic Control Panel
Classic Control Panel has the following admins and groups by default:
Default administrative user | Group membership |
|---|---|
uid=aciadmin,ou=globalusers,cn=config | Member of the ACI Administrator Group. |
uid=namespaceadmin,ou=globalusers,cn=config | Member of the Namespace Administrator Group. |
uid=operator,ou=globalusers,cn=config | Member of the Operator Group. |
uid=schemaadmin,ou=globalusers,cn=config | Member of the Schema Administrator Group. |
uid=superadmin,ou=globalusers,cn=config | Member of the Directory Administrator Group. |
uid=icsadmin,ou=globalusers,cn=config | Member of the ICS Administrator Group. |
uid=icsoperator,ou=globalusers,cn=config | Member of the ICS Operator Group. |
uid=readonly,ou=globalusers,cn=config | Member of the Read Only Group. |
The roles and corresponding required permissions are described in the table below.
Role | Required Permissions (Value of vdPrivilege) |
|---|---|
Directory Administrator | admin-write |
Read Only | config-read |
Namespace Administrator | config-readconfig-write |
Operator | config-read |
Schema Administrator | config-read |
ACI Administrator | config-read |
ICS Administrator | config-read |
ICS Operator | config-read |
ICS Operator | config-read |
File Manager Admin | file-manager-read |
New Control Panel
For the new Control Panel, each class of permissions matches a section in the left navigation menu.
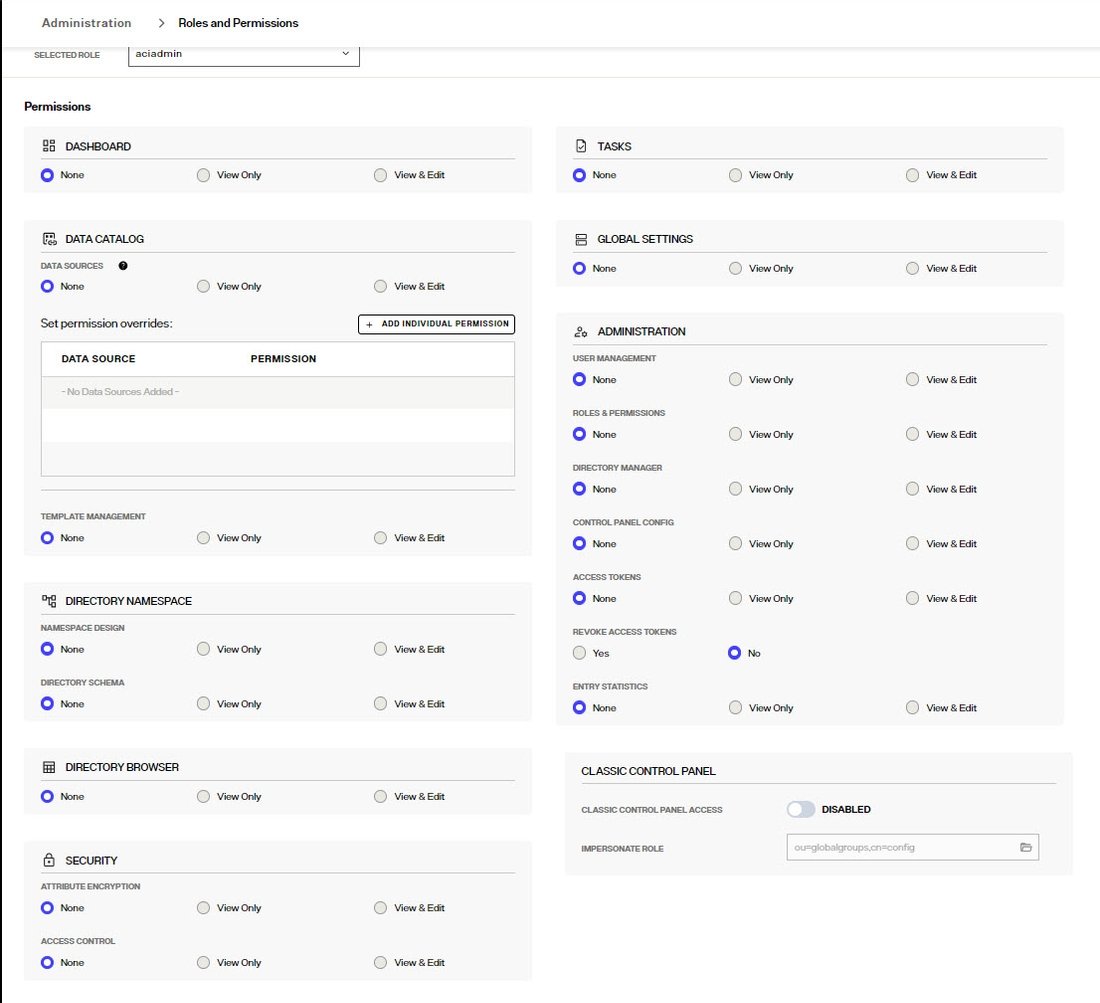
- DATA CATALOG: Assign permissions to configure and manage data sources with the ability to set specific permission overrides for specific data sources. For example, you can assign a set of users permissions to manage and use a specific set of data sources. The data sources must be defined prior to assigning permisssions.
- DIRECTORY NAMESPACE: Assign permissions to namespace design (where identity views are created from) and directory schema (where the LDAP directory schema is managed).
- DIRECTORY BROWSER: Assign permissions to the Directory Brower where entries in the RadiantOne namespace can be managed.
- SECURITY: Assign permissions to configure attribute encryption and access controls.
- TASKS: Various actions (e.g. initializing a RadiantOne directory) are launched as tasks. Use this to assign permissions for admins that can manage tasks (e.g. change JVM settings, modify task schedules, delete tasks...etc.).
- GLOBAL SETTINGS: Assign permissions to configuration for LDAP access (supported directory controls and user to DN mapping), and the client certificate truststore (to manage client certificates for SSL/TLS communications.
- ADMINISTRATION: Assign access to user management, roles & permissions, directory manager settings, control panel configuration, access tokens and entry statistics.
- CLASSIC CONTROL PANEL: enable or disable access to the Classic Control Panel and indicate what role (identified by group membership) should be enforced in the Classic Control Panel. This is to allow administrators the needed access to both the new and Classic Control Panels.
Assigning Users to Roles
Admin users can be assigned to roles from Control Panel > Admin > User Management tab. Either search for a user to manage their roles, or click CREATE USER to create a new user and assign their roles during the creation.
Creating Users
- From Control Panel > Admin > User Management tab, click CREATE USER.
- Enter a username.
- Enter a passwod.
- Confirm the password.
- Enter a first name.
- Enter a last name.
- Enter an email address.
- Toggle the status to either active or inactive. Inactive users are not allowed to log into Control Panel.
- To assign roles, select a role from the drop-down list and click +ASSIGN ROLE. Repeat this step until all roles are selected.
- Click CREATE.
Assigning Roles to Existing Users
-
From Control Panel > Admin > User Management tab, search for a user and click on the username to select it.
-
Locate the Assign Roles section.
-
Select a role from the drop-down list and click +ASSIGN ROLE. Repeat this step until all roles are selected.
-
Click SAVE
Customizing the Classic Control Panel
The following settings are currently only applicable to the Classic Control Panel.
To switch to Classic Control Panel, use the menu options for the logged in user in the upper right.

Color theme
The Classic Control Panel can have a custom color theme.
Message of the Day
The Classic Control Panel login page contains a basic username and password text box. To add a custom message on the login page, follow the steps below.
- Switch to the Classic Control Panel as a member of the Directory Administrators role.
- Go to the Settings tab > Server Front End > Administration.
- In the Message of the Day Configuration, enter the message contents.
- Enter a message title (will display if a popup window is used).
- (Optional) check the box to enable a "Warning" icon if you want the message to be prefixed with a "Warning".
- (Optional) check the box to enable a "Popup" message that displays the message title and contents that the user must explicitly acknowledge and close.
- Click Save.
- Log out of the Classic Control Panel to be returned to the login screen to view the custom message.
An example of a custom message on the login page is shown below.
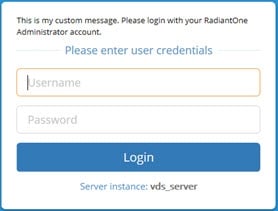
An example of a custom message using the "Warning" icon on the login page is shown below.
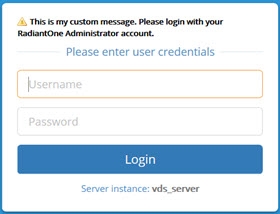
An example of a custom message using the "Popup" on the login page is shown below.

Banner
A custom message can be added to the banner of RadiantOne User Interface pages. This includes the Classic Control Panel, the Server Control Panel, the login page, and the logout landing page.
To add a custom message:
-
Log into the Classic Control Panel as a member of the Directory Administrators role.
-
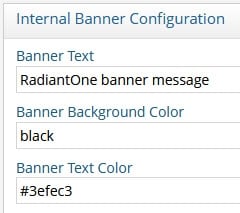
Navigate to Settings > Administration > Internal Banner Configuration section.
-
Enter the message to appear in the banner in the Banner Text field.
-
Specify a color in the Banner Background Color field. You can indicate the color by name or by hex color code.
NoteIf you enter a hex color code, include the "#" character here. If the color specified is not recognized, it defaults to gray.
-
Specify the banner's text color. You can indicate the color by name or by hex color code.
NoteIf you enter a hex color code, include the "#" character here. If the color specified is not recognized, it defaults to gray.
-
Click Save. The next time the Classic Control Panel is opened (or the browser tab is refreshed), the custom banner message is displayed.
Navigating the Control Panel
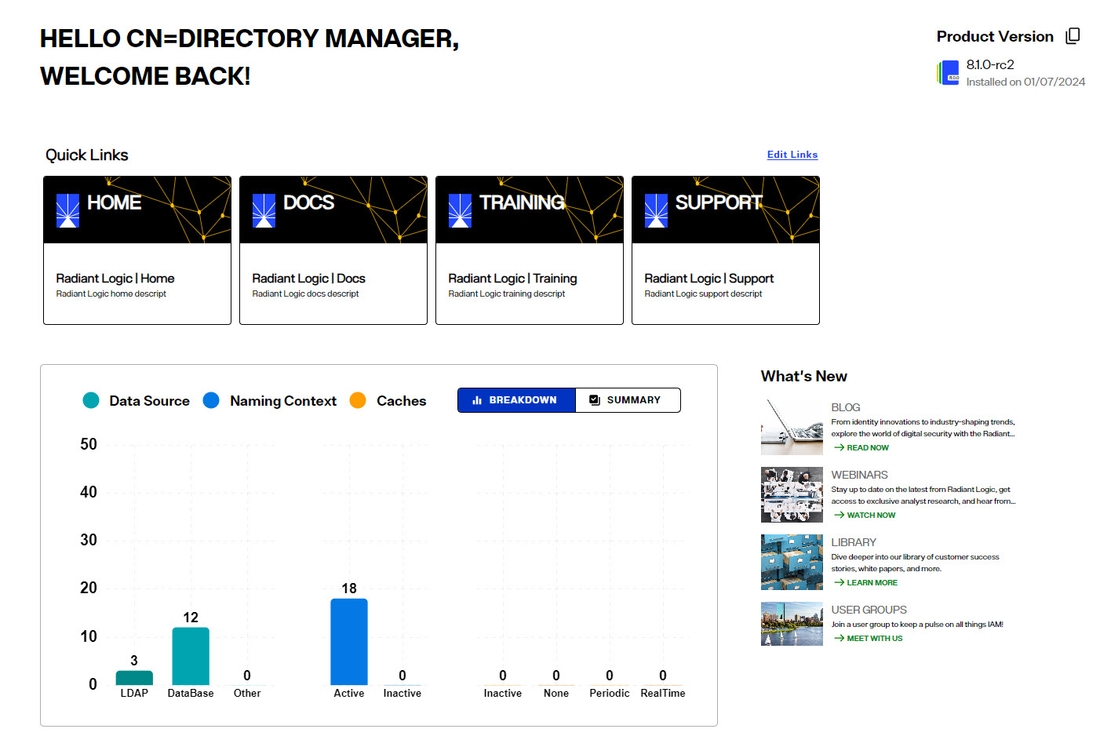
Dashboard
The Dashboard displays some quick links (editable), links to valuable Radiant Logic Marketing content like blogs, white papers and webinars, and a summary chart breakdown of how RadiantOne has been configured: number of data sources, caches, and naming contexts.
You can also view and copy the version of RadiantOne in the upper-right.
Setup
The setup section contains the Data Catalog where connections to identity sources are configured and Directory Namespace where identity views are defined.
Data Catalog
Data Sources - Data Sources repesent connections to identity sources. For details see: Managing Data Sources
Schemas - Schemas contain the metadata extracted from data sources. This metadata is used to create identity views. For details see: Managing Schemas
Drivers and Templates - Drivers and templates are used to establish connections to identity sources. For details see: Managing Drivers and Templates
Directory Namespace
The RadiantOne namespace can be comprised of many different root naming contexts. Each one can represent a different type of backend configuration. This might be a RadiantOne Directory store, or an identity view created from a data source (LDAP, database, or custom). The configuration of the namespace is managed in the Namespace Design section. The LDAP schema for RadiantOne is configured in the Directory Schema section.
Namespace Design - The RadiantOne namespace is managed from here. Create and manage RadiantOne Directory stores, identity views, and persistent cache from here. For details, see: Managing Directory Stores and Managing Identity Views.
Directory Schema - The RadiantOne LDAP directory schema is managed from here. For details, see: Managing Directory Schema.
Global Identity Builder - The Global Identity Builder is only access in the Classic Control Panel.
To switch to Classic Control Panel, use the menu options for the logged in user in the upper right.

The currently logged in user must have permissions to access the Classic Control Panel.
Manage
The Manage section contains the Directory Browser where the runtime directory tree can be accessed, a Tasks section where tasks can be managed, and a Security section where security (e.g. access controls, attribute encryption...etc.) can be configured from.
Directory Browser
Entries can be managed from the Directory Browser.
Tasks
Manage Tasks from here.
Security
Attribute Encryption - Manage Attribute Encryption from here.
Password Policies - Manage Password Policies from Classic Control Panel.
Access Controls - Manage Access Controls from here.
Global settings
The Global Settings section is where client access protocols (LDAP, SCIM, REST) are managed from. Client certificates for TLS communication are also managed here. Token Validators, tuning limits and global attribute handling are also managed in this section.
Client Protocols - Manage supported LDAP controls and user-to-DN mapping from the Control Panel > Global Settings > Client Protocols > LDAP.
Manage the SCIM interface from Classic Control Panel.
Manage the REST interface from Classic Control Panel.
Client Certificates - Manage client certificates from the Control Panel > Global Settings > Client Certificates.
Token Validators - External token validators allow applications to use an access token to call an API on behalf of itself. The API then responds with the requested data. For details on configuring external token validators, see: External Token Validators.
Tuning - Tuning topics include Limits, General Attributes Handline, Changelog Settings, and Log Settings.
Changelog - The changelog is one of the recommended approaches for other processes to detect changes that have happened to RadiantOne entries. For details, please see: Changelog
Log Settings - RadiantOne supports logging at different levels for different components. Logs for the different components are configured in the Classic Control Panel > Settings > Logs section. For details, please see: Log Settings
Admin
The Admin section is used for managing admin users, delegated roles and permissions, directory manager settings, control panel configurations, access tokens and view entry statistics reports.
User Management
Manage delegated admin users from here.
Roles & Permissions
Manage default and custom roles from here.
Directory Admin Settings
Directory Manager Account The directory manager (cn=directory manager by default) is the super user for the directory and this account is defined during the RadiantOne install. For details on defining this account, see the Environment Operations Center Guide.
The super user is the only user that can log into the Control Panel while RadiantOne is not running. When you log into the Control Panel with this user, you can perform any of the operations described in Delegated Administration. Also, access permissions and password policies do not apply for this user. This safety measure prevents someone from accidentally denying the rights needed to access and manage the server. Access to this super user account should be limited. If you require many directory managers, add these as members to the Directory Administrator Role instead of having them all use the single super user account.
The RadiantOne super user account is associated with an LDAP entry in the RadiantOne namespace located at: cn=Directory Manager,ou=RootUsers,cn=config. Cn=Directory Manager,ou=RootUsers,cn=config is authorized the same as cn=Directory Manager.
To configure the Directory Manager username:
-
From Control Panel > Admin > Directory Manager Settings tab, locate the Directory Manager Account settings.
-
Enter the value in the USERNAME property.
WarningThe new value of the parameter should be in the same syntax:
cn=<new user value>. -
Click SAVE.
-
Restart the RadiantOne service.
-
Re-open the Control Panel.
-
Log in as the new username.
If you update the Directory Manager username, the LDAP entry in the RadiantOne namespace is located at: cn=Directory Manager,ou=RootUsers,cn=config is updated with a seeAlso attribute that contains the value of the new username. This allows the new username to be used to log into the Control Panel.
Directory Manager Password
The directory administrator (e.g. cn=directory manager) password is set during the install of RadiantOne and can be updated in Control Panel. You must know the current password to update the password. To change this password, from the Control Panel > Admin > Directory Manager Settings tab, locate the Directory Manager Account settings. Click
 an enter the old (current) password and the new value. Confirm the new value and click SAVE PASSWORD.
an enter the old (current) password and the new value. Confirm the new value and click SAVE PASSWORD.
If you change the password and you are currently logged into the Control Panel as the directory administrator, you must close the Control Panel and re-open it logging in with the new password.
You can also change the directory administrator’s password via LDAP. The DN representing the directory administrator is: cn=Directory Manager,ou=RootUsers,cn=config. The example below is using an LDIF file and the ldapmodify command to modify the password:
dn: cn=Directory Manager,ou=RootUsers,cn=config
changetype: modify
replace: userPassword
userPassword: newpassword
An example of the syntax used in the command is shown below, assuming the LDIF file described above is named ChangePassword.ldif. You must bind as the cn=directory manager with the current password in order to update the password with this LDAP command.
ldapmodify.exe -D "cn=Directory Manager,ou=RootUsers,cn=config" -w currentpassword -h localhost -p 2389 -f c:\radiantone\ChangePassword.ldif
The RadiantOne service may be running when this command is executed.
You can also change the directory administrator's password via REST (ADAP API). The following commands can be issued from a Linux client that is able to connect to the RadiantOne service's REST endpoint. Set the following on the Linux client:
REST_ENDPOINT="https://localhost:9101"
BIND_DN="cn=Directory Manager"
BIND_USER_DN="cn=Directory Manager,ou=rootusers,cn=config"
CURRENT_PASSWORD="MySuperSecretPassw0rd2"
NEW_PASSWORD="MySuperSecretPassw0rd3"
BASE64_USERNAME_PASSWORD=$(echo -n $BIND_DN:$CURRENT_PASSWORD | base64)
Run the following curl command on the Linux client:
curl -k --location --request PATCH "$REST_ENDPOINT/adap/$BIND_USER_DN" \
--header "Content-Type: application/json" \
--header "Authorization: Basic $BASE64_USERNAME_PASSWORD" \
--data '{
"params": {
"mods": [
{
"attribute": "userPassword",
"type": "REPLACE",
"values": [
"'$NEW_PASSWORD'"
]
}
]
}
}'
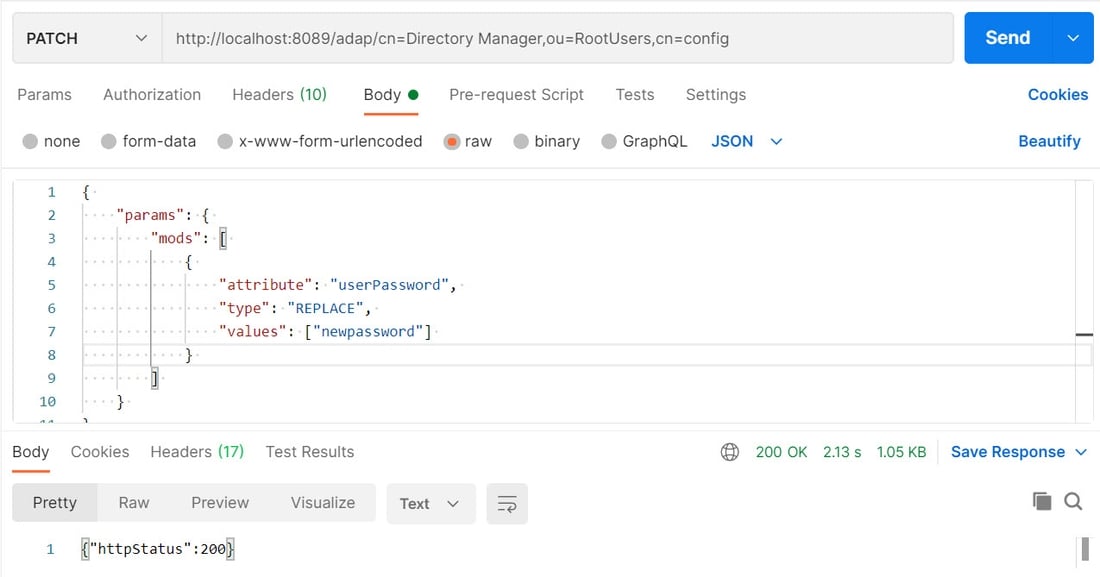
If the command is successful, an HTTP status of 200 is returned: {"httpStatus":200}
An example of using Postman as a REST client to update the cn=directory manager password is shown below.
- Add an Authorization header that contains Basic with the base 64 encoded value for cn=directory manager:currentpassword. Use cn=directory manager in the authorization header value, not cn=Directory Manager,ou=RootUsers,cn=config. E.g.
Basic Y249RGlyZWN0b3J5IE1hbmFnZXI6bmV3cGFzc3dvcmQxMjM=
 2. Issue a PATCH operation with
2. Issue a PATCH operation with http://RESTENDPOINT:8089/adap/cn=Directory Manager,ou=RootUsers,cn=config with the following body:
{
"params": {
"mods": [
{
"attribute": "userPassword",
"type": "REPLACE",
"values": ["newpassword"]
}
]
}
}
Administrators Group DN
This parameter can be set to the DN of the Administrators group defined in the virtual namespace. The administrators group is checked for authorization purposes as members of this group do not have limits or password policy enforced for them. To manage this value, from the Control Panel > Admin > Directory Manager Settings Tab > Special Group section. Enter the value of a valid group DN located in the RadiantOne namespace.

Control Panel Configuration
Manage the OIDC Provider Configuration to support SSO into Control Panel from here.
Access Tokens
Manage Access Tokens from here.
Entry Statistics
Run Entry Statistics Reports from here.
File Manager
File Manager is only accessible in the Classic Control Panel.
RadiantOne does not allow access to files via operating system user interfaces. The File Manager option allows you to view, upload, and download files that reside under the RLI_HOME directory. It also allows you to build jar files. To access the File Manager, in the Classic Control Panel, go to Settings > Configuration > File Manager. The admin that accesses Classic Control Panel must be assigned to a role that impersonates a role (e.g. Directory Administrators and FileManagerAdmin) that has file-manager-read and/or file-manager-write vdPrivilege to read (file-manager-read) and/or read and manage (file-manager-write) files from File Manager. By default only the Directory Administrators and FileManagerAdmin roles have these privileges in Classic Control Panel.
The default location displayed in File Manager is RLI_HOME.
Files at the RLI_HOME level cannot be modified with File Manager.

To navigate within File Manager, click a folder in the main File Manager pane, or click a link the navigation bar at the top of the File Manager. To go up one folder, click the up-arrow button.
Some files types are hidden from view in File Manager. These file types include the following.
- .cer
- .keystore
- .truststore
Uploading Files
Uploads can be made anywhere within the <RLI_HOME>, except within <RLI_HOME> itself.
To upload a file, click Upload Files. In the File Upload window, navigate to the file to be uploaded, select the file, and click Open.
Actions Drop-down Menu
The Actions drop-down menu allows perform the following functions.
- Download files
- Delete files
- Open a selection
- Clear a selection
Downloading Files
To download a file in File Manager, navigate in File Manager to the file's location. From the Actions drop-down menu, select Download Files.
Deleting Files
The Delete Files option allows you to delete one file at a time. To delete a file in File Manager, navigate to the file's location. From the Actions drop-down menu, selct Delete Files. The file is downloaded to the location indicated by your web browser.
Open Selection
Some files, such as text, LDIF, XML, and jar files are viewable in File Manager. To view a file in File Manager, navigate to the file's location. From the Actions drop-down menu, select Open Selection.
Files such as .class files are not openable in File Manager.
Building Jar Files
The File Manager allows you to build jar files.
To build jar files:
-
In the Classic Control Panel, click Settings > Configuration > File Manager.
-
In File Manager, browse to RLI_HOME/vds_server/custom or any folder within. In the menu bar beneath the navigation bar, the Build drop-down menu displays.

-
From the Build drop-down menu, select an option.

Switch to Classic Control Panel
Some settings must be managed using the RadiantOne Classic Control Panel. To switch to Classic Control Panel, use the menu options for the logged in user in the upper right.

To reach the Server Control Panel from within the Classic Control Panel, click the Server Control Panel link at the top right. The Server Control Panel can be used for some service monitoring dashboards and accessing log files.
The following settings must be managed from the RadiantOne Classic Control Panel:
- Synchronization: Classic Control Panel > Synchronization tab
See Synchronization for details. - Password Policies: Classic Control Panel > Settings > Security > Password Policies
See Password Policies for details. - SCIM config (frontend): Classic Control Panel > Settings > Server Front End > SCIM
See SCIM for details. - REST config (frontend): Classic Control Panel > Settings > Server Front End > Other Protocols
See REST for details. - External Token Validators: Classic Control Panel > Settings > Security > External Token Validators
See External Token Validators for details. - Limits: Classic Control Panel > Settings > Limits
See Limits for details. - Attribute Handling: Classic Control Panel > Settings > Server Front End > Attributes Handling
See General Attribute Handling for details. - Duplicates Handling: Classic Control Panel > Settings > Server Front End > Duplicates Handling See Duplicates Handling for details.
- Changelog Settings: Classic Control Panel > Settings > Logs > Changelog
See Changelog for details. - Log Settings: Classic Control Panel > Settings > Logs > Log Settings
See Log Settings for details. - Control Panel customizations (lock, color theme, session timeout, max users, banner, custom message on login screen): Classic Control Panel > Settings > Server Front End > Administration
See Customizing the Classic Control Panel for details. - PCache Refresh Monitoring: Classic Control Panel > PCache Monitoring tab
See Persistent Cache Refresh Monitoring for details. - Intercluster Replication Monitoring: Classic Control Panel > Replication Monitoring tab
See Replication Monitoring for details. - File Manager: Classic Control Panel > Settings > Configuration > File Manager
See File Manager for details. The admin that accesses Classic Control Panel must be assigned to a role that impersonates a role (e.g. Directory Administrators and FileManagerAdmin) that has file-manager-read and/or file-manager-write vdPrivilege to read (file-manager-read) and/or read and manage (file-manager-write) files from File Manager. By default only the Directory Administrators and FileManagerAdmin roles have these privileges in Classic Control Panel. - Identity Data Analysis Wizard: Classic Control Panel > Wizards > Identity Data Analysis. See Identity Data Analysis for details.
- Global Identity Builder: Classic Control Panel > Wizards > Global Identity Builder. See Global Identity Builder for details.